Kryptos Threat Intelligence
Kryptos Threat Intelligence enables entreprises solutions to TRUST employee’s mobile work devices just like they TRUST other company assets like Servers, gateways, networking hardware, desktops, and laptops. Very few if any SIEM tools support extraction of features from mobile devices and provide mobile threat intelligence.
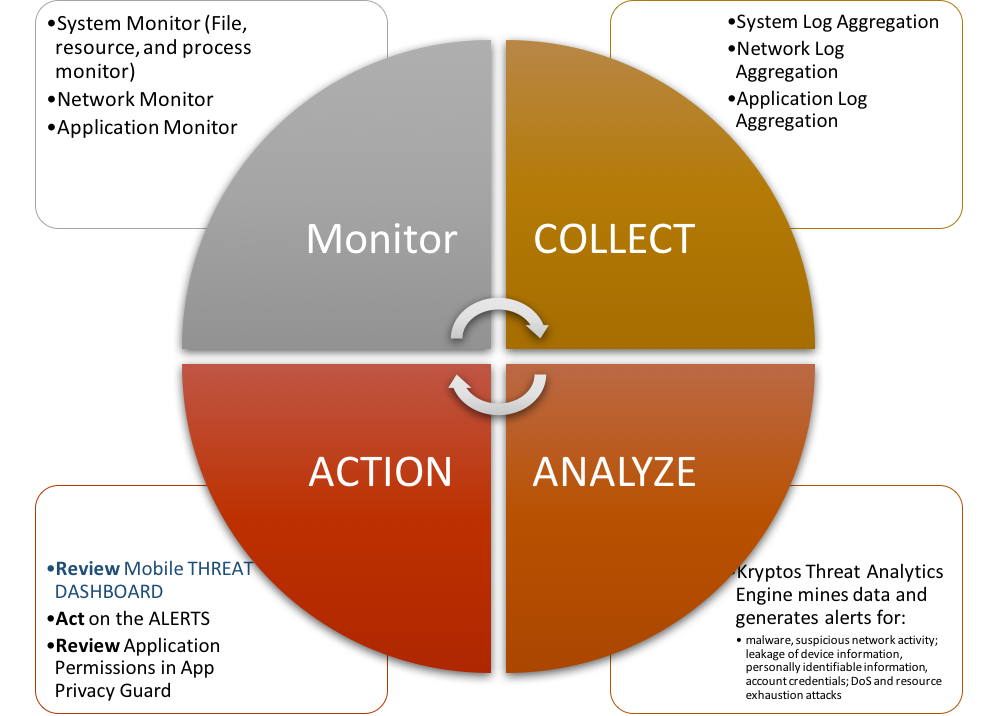
Kryptos Threat Intelligence app high level architecture involves four steps at system, network, and apps layers:
- Monitor device
- Collect logs
- Analyze
- Act on threats
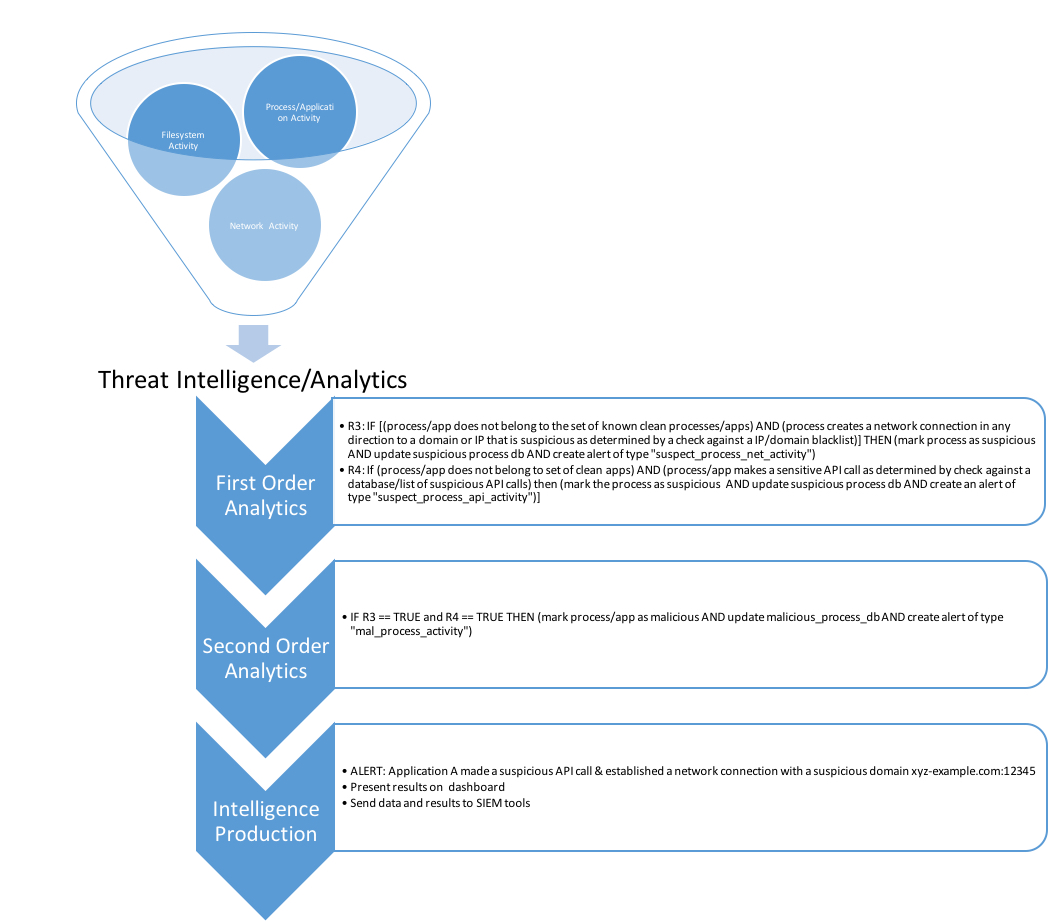
Threat analtics is built upon two key components:
- Behavioral rule engine
- Support Vector Machine Engine
Analytics engine runs first and second order rules on collected data. We improve accuracy with self-learning algorithm and real-time user feedbbcak.